Owasp Api Security Top 10 2023: Comprehensive Security Guide

Owasp Api Security Top 10 2023: Comprehensive Security Guide
Published 9/2024
MP4 | Video: h264, 1920x1080 | Audio: AAC, 44.1 KHz
Language: English | Size: 6.86 GB | Duration: 12h 13m
Explore key API security concepts through real examples during the development of web applications
What you'll learn
Understand the OWASP API Top 10 vulnerabilities and their impact on security
Learn best practices for securing APIs against common threats
Identify key tools and techniques for API security assessment
Gain hands-on experience with real-world API security scenarios
Explore mitigation strategies for each OWASP vulnerability
Develop a robust API security strategy for your applications
Understand the importance of authentication and authorization in APIs
Learn how to perform effective security testing on APIs
Learn how to secure sensitive data in API responses
Explore the risks of improper CORS configurations in APIs
Understand the implications of using third-party APIs securely
Gain skills in implementing OAuth and JWT for API security
Discover how to handle API versioning securely
Learn about the security aspects of API design and architecture
Understand the role of security audits and reviews in API development
Get practical tips for threat modeling specific to APIs
Explore strategies for incident response in API security breaches
Requirements
Basic understanding of web development concepts
Familiarity with RESTful APIs and HTTP protocols
Knowledge of security principles is a plus but not mandatory
No specific tools are required; just a computer with internet access
A willingness to learn and explore API security topics
Description
APIs are the digital highways that connect modern applications, enabling seamless communication between systems, services, and devices. But with great power comes great responsibility—APIs have become one of the most common attack vectors for malicious actors. If you're developing, deploying, or managing APIs, understanding how to secure them is no longer optional—it's essential.Welcome to the "OWASP API Top 10 2023" course, your step-by-step guide to mastering API security. This course is designed to take you from the basics to advanced protection strategies, all while focusing on the latest OWASP API Top 10 vulnerabilities that pose real threats to your applications.You'll explore key security concepts not just in theory, but through practical, real-world examples. From the very start, you'll get your hands dirty by diving into the development of web applications that mirror the security challenges professionals face every day. With these real-world examples, you'll learn how to identify, mitigate, and prevent the most critical vulnerabilities that hackers exploit, such as:Broken Object-Level AuthorizationMass AssignmentSecurity MisconfigurationLack of Rate LimitingAnd many more!This course will guide you through:Understanding the OWASP API Top 10 2023 vulnerabilities: What are they? Why do they matter? How can they cripple your application security if left unchecked?Real-world scenarios and practical examples: See how attackers exploit these vulnerabilities and how you can prevent it.Building secure APIs from the ground up: Learn how to develop APIs with security embedded into each stage of the development lifecycle.Mitigation strategies: You'll not only learn how to detect vulnerabilities but also implement robust security measures to protect your API and the sensitive data it handles.Security best practices: Gain insights into proper authentication, authorization, input validation, rate limiting, and more.Whether you're a developer looking to build more secure APIs, a security professional wanting to expand your skill set, or an IT leader responsible for protecting your organization's data, this course is perfect for you. The content is designed to be beginner-friendly, but it also offers deep dives into complex security topics that even seasoned developers and security experts will find valuable.By the end of the course, you'll not only be familiar with the OWASP API Top 10 list but also be equipped to confidently build, test, and secure APIs against the latest threats. You'll walk away with practical skills and knowledge that can be applied immediately to your projects, helping you build secure, resilient APIs that can stand up to even the most sophisticated attacks.Why enroll in this course?Hands-on learning: You won't just watch; you'll actively work through real security issues.Up-to-date with OWASP API Top 10 2023: Learn the latest threats and defenses.Expert guidance: Get insights from instructors who specialize in API security.Actionable insights: Gain techniques you can use right away in your job or project.Certificate of completion: Add a valuable credential to your resume and boost your career.Don't wait until your APIs are under attack—take control of your API security now. Enroll today and take the first step towards becoming an expert in API security!
Overview
Section 1: Introduction
Lecture 1 Communication plan
Section 2: OWASP API Top 10 2023
Lecture 2 OWASP API Security Project & OWASP API Security Top 10 2023
Lecture 3 API1:2023 Broken Object Level Authorization - Part 1
Lecture 4 API1:2023 Broken Object Level Authorization - Part 2 (Practice)
Lecture 5 API1:2023 Broken Object Level Authorization - Part 3 (Zero-Trust, UUIDs)
Lecture 6 API2:2023 Broken Authentication - Part 1 (Basics, Impact, Types of Attacks)
Lecture 7 API2:2023 Broken Authentication - Part 2 (Case Studies, OAuth, OpenID)
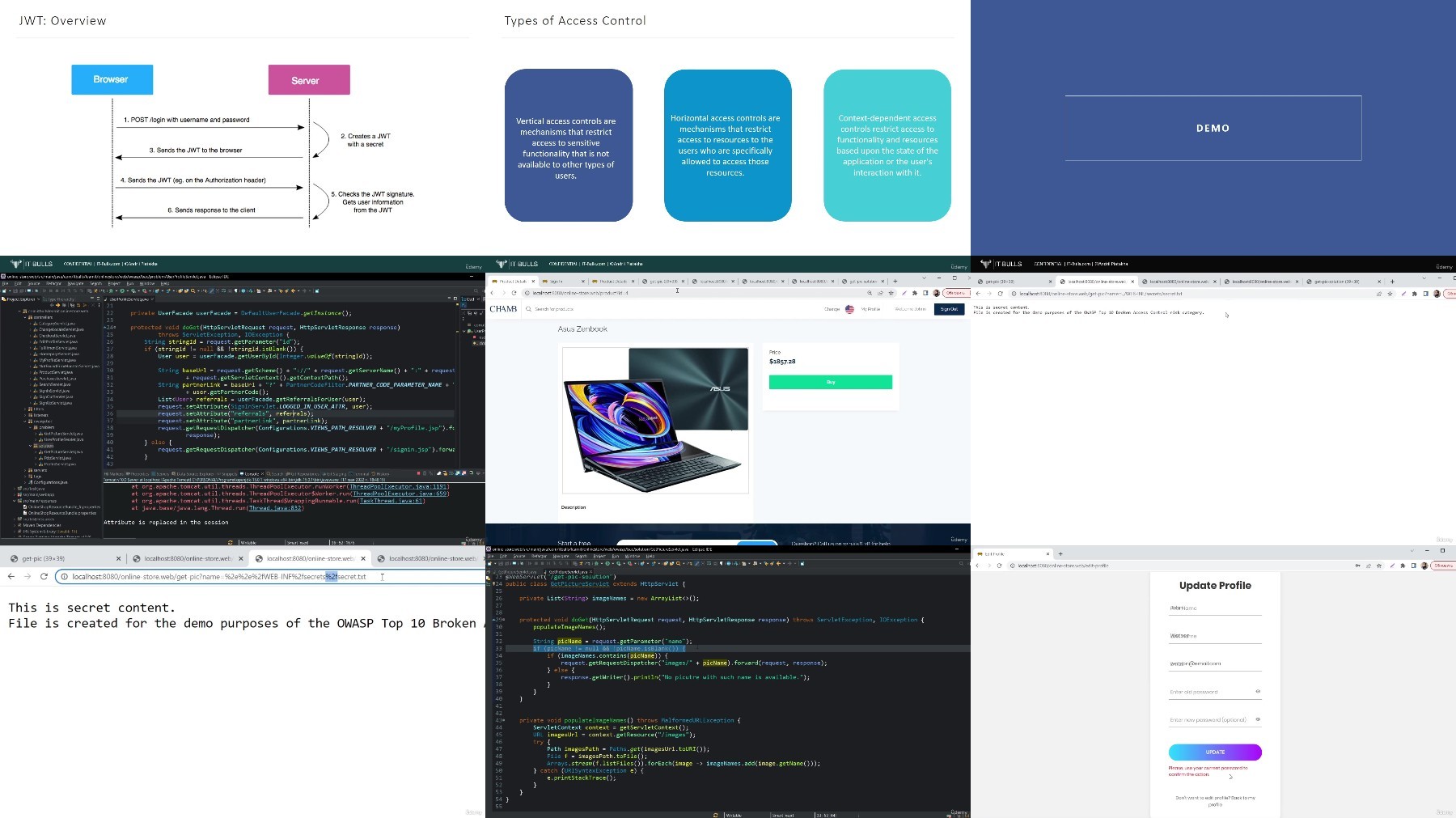
Lecture 8 API2:2023 Broken Authentication - P.3 - (Practice, JWT Tokens, Timing Attacks)
Lecture 9 API3:2023 Broken Object Property Level Authorization - Part 1
Lecture 10 API3:2023 Broken Object Property Level Authorization - Part 2 (Practice)
Lecture 11 API4:2023 Unrestricted Resource Consumption - Part 1
Lecture 12 API4:2023 Unrestricted Resource Consumption - Part 2 (Practice)
Lecture 13 API5:2023 Broken Function Level Authorization - Part 1
Lecture 14 API5:2023 Broken Function Level Authorization - Part 2 (Practice)
Lecture 15 API6:2023 Unrestricted Access to Sensitive Business Flows - Part 1
Lecture 16 API6:2023 Unrestricted Access to Sensitive Business Flows - Part 2
Lecture 17 API6:2023 Unrestricted Access to Sensitive Business Flows - Part 3 (Practice)
Lecture 18 API7:2023 - Server Side Request Forgery
Lecture 19 API8:2023 - Security Misconfiguration
Lecture 20 API9:2023 Improper Inventory Management - Part 1
Lecture 21 Improper Inventory Management - Part 2 (Practice)
Lecture 22 API10:2023 Unsafe Consumption of APIs - Part 1
Lecture 23 API10:2023 Unsafe Consumption of APIs - Part 2 (Practice)
Section 3: Extra Materials: OWASP Top 10 2021
Lecture 24 OWASP Top 10: Overview
Lecture 25 Broken Access Control
Lecture 26 Cryptography Failures (Theory, Sensitive Data, Data Breach, Types of Failures)
Lecture 27 Cryptography Failures (Practical Examples, SQL Injections, TLS/SSL, HTTPS)
Lecture 28 Cryptography Failures (Examples, Password Encryption, Hashing, Salting)
Lecture 29 Injection (Overview, Fuzzing, CWEs, Impact, Injection Types, Command Injection)
Lecture 30 Injection (Cross Site Scripting, Types of XSS, SQL, JPA, NoSQL Injections)
Lecture 31 Injection (XPath Injection, Log Injection, Input Validation)
Lecture 32 Insecure Design (Overivew, CWEs, Shift Left Security, Threat Modeling Manifesto)
Lecture 33 Insecure Design (Secure Design Process, Security Controls, Metrics, Examples)
Lecture 34 Security Misconfiguration (Overview, CWEs, Types, Real-life attacks)
Lecture 35 Security Misconfiguration (Hardening, Zero Trust, Defense in Depth, Practice)
Lecture 36 Vulnerable & Outdated Components
Lecture 37 Identification & Authentication Failures
Lecture 38 Software & Data Integrity Failures
Lecture 39 Security Logging & Monitoring Failures
Lecture 40 Server-Side Request Forgery (SSRF)
Section 4: Bonus section
Lecture 41 Bonus lesson
Developers looking to enhance their API security skills,Security professionals seeking to understand the latest API vulnerabilities,Software engineers interested in building secure applications,Students and beginners eager to learn about API security best practices,Tech leads and architects wanting to implement robust security measures in their projects
https://ddownload.com/9kfd1flcq7uy/Udemy_OWASP_API_Security_Top_10_2023_Comprehensive_Security_Guide_2024-9_Downloadly.ir.part1.rar
https://ddownload.com/n6lg17qdwee1/Udemy_OWASP_API_Security_Top_10_2023_Comprehensive_Security_Guide_2024-9_Downloadly.ir.part2.rar
https://ddownload.com/v63qdid8gm2l/Udemy_OWASP_API_Security_Top_10_2023_Comprehensive_Security_Guide_2024-9_Downloadly.ir.part3.rar
https://ddownload.com/fb32p6mmbp7m/Udemy_OWASP_API_Security_Top_10_2023_Comprehensive_Security_Guide_2024-9_Downloadly.ir.part4.rar
https://rapidgator.net/file/7b11c66c8ea7c4de0c72d1c32c64f03b/Udemy_OWASP_API_Security_Top_10_2023_Comprehensive_Security_Guide_2024-9_Downloadly.ir.part1.rar
https://rapidgator.net/file/447ac870cca39b54be3141a588d8bb02/Udemy_OWASP_API_Security_Top_10_2023_Comprehensive_Security_Guide_2024-9_Downloadly.ir.part2.rar
https://rapidgator.net/file/91c38fe2e817a33ddffb1f83efb616ab/Udemy_OWASP_API_Security_Top_10_2023_Comprehensive_Security_Guide_2024-9_Downloadly.ir.part3.rar
https://rapidgator.net/file/64859c9d6063240bd3003011588fad65/Udemy_OWASP_API_Security_Top_10_2023_Comprehensive_Security_Guide_2024-9_Downloadly.ir.part4.rar
https://turbobit.net/k0bcxas1k1en/Udemy_OWASP_API_Security_Top_10_2023_Comprehensive_Security_Guide_2024-9_Downloadly.ir.part1.rar.html
https://turbobit.net/xypghk5tf504/Udemy_OWASP_API_Security_Top_10_2023_Comprehensive_Security_Guide_2024-9_Downloadly.ir.part2.rar.html
https://turbobit.net/jl2j0lg9j60x/Udemy_OWASP_API_Security_Top_10_2023_Comprehensive_Security_Guide_2024-9_Downloadly.ir.part3.rar.html
https://turbobit.net/d7e4ypt02sdf/Udemy_OWASP_API_Security_Top_10_2023_Comprehensive_Security_Guide_2024-9_Downloadly.ir.part4.rar.html
What you'll learn
Understand the OWASP API Top 10 vulnerabilities and their impact on security
Learn best practices for securing APIs against common threats
Identify key tools and techniques for API security assessment
Gain hands-on experience with real-world API security scenarios
Explore mitigation strategies for each OWASP vulnerability
Develop a robust API security strategy for your applications
Understand the importance of authentication and authorization in APIs
Learn how to perform effective security testing on APIs
Learn how to secure sensitive data in API responses
Explore the risks of improper CORS configurations in APIs
Understand the implications of using third-party APIs securely
Gain skills in implementing OAuth and JWT for API security
Discover how to handle API versioning securely
Learn about the security aspects of API design and architecture
Understand the role of security audits and reviews in API development
Get practical tips for threat modeling specific to APIs
Explore strategies for incident response in API security breaches
Requirements
Basic understanding of web development concepts
Familiarity with RESTful APIs and HTTP protocols
Knowledge of security principles is a plus but not mandatory
No specific tools are required; just a computer with internet access
A willingness to learn and explore API security topics
Description
APIs are the digital highways that connect modern applications, enabling seamless communication between systems, services, and devices. But with great power comes great responsibility—APIs have become one of the most common attack vectors for malicious actors. If you're developing, deploying, or managing APIs, understanding how to secure them is no longer optional—it's essential.Welcome to the "OWASP API Top 10 2023" course, your step-by-step guide to mastering API security. This course is designed to take you from the basics to advanced protection strategies, all while focusing on the latest OWASP API Top 10 vulnerabilities that pose real threats to your applications.You'll explore key security concepts not just in theory, but through practical, real-world examples. From the very start, you'll get your hands dirty by diving into the development of web applications that mirror the security challenges professionals face every day. With these real-world examples, you'll learn how to identify, mitigate, and prevent the most critical vulnerabilities that hackers exploit, such as:Broken Object-Level AuthorizationMass AssignmentSecurity MisconfigurationLack of Rate LimitingAnd many more!This course will guide you through:Understanding the OWASP API Top 10 2023 vulnerabilities: What are they? Why do they matter? How can they cripple your application security if left unchecked?Real-world scenarios and practical examples: See how attackers exploit these vulnerabilities and how you can prevent it.Building secure APIs from the ground up: Learn how to develop APIs with security embedded into each stage of the development lifecycle.Mitigation strategies: You'll not only learn how to detect vulnerabilities but also implement robust security measures to protect your API and the sensitive data it handles.Security best practices: Gain insights into proper authentication, authorization, input validation, rate limiting, and more.Whether you're a developer looking to build more secure APIs, a security professional wanting to expand your skill set, or an IT leader responsible for protecting your organization's data, this course is perfect for you. The content is designed to be beginner-friendly, but it also offers deep dives into complex security topics that even seasoned developers and security experts will find valuable.By the end of the course, you'll not only be familiar with the OWASP API Top 10 list but also be equipped to confidently build, test, and secure APIs against the latest threats. You'll walk away with practical skills and knowledge that can be applied immediately to your projects, helping you build secure, resilient APIs that can stand up to even the most sophisticated attacks.Why enroll in this course?Hands-on learning: You won't just watch; you'll actively work through real security issues.Up-to-date with OWASP API Top 10 2023: Learn the latest threats and defenses.Expert guidance: Get insights from instructors who specialize in API security.Actionable insights: Gain techniques you can use right away in your job or project.Certificate of completion: Add a valuable credential to your resume and boost your career.Don't wait until your APIs are under attack—take control of your API security now. Enroll today and take the first step towards becoming an expert in API security!
Overview
Section 1: Introduction
Lecture 1 Communication plan
Section 2: OWASP API Top 10 2023
Lecture 2 OWASP API Security Project & OWASP API Security Top 10 2023
Lecture 3 API1:2023 Broken Object Level Authorization - Part 1
Lecture 4 API1:2023 Broken Object Level Authorization - Part 2 (Practice)
Lecture 5 API1:2023 Broken Object Level Authorization - Part 3 (Zero-Trust, UUIDs)
Lecture 6 API2:2023 Broken Authentication - Part 1 (Basics, Impact, Types of Attacks)
Lecture 7 API2:2023 Broken Authentication - Part 2 (Case Studies, OAuth, OpenID)
Lecture 8 API2:2023 Broken Authentication - P.3 - (Practice, JWT Tokens, Timing Attacks)
Lecture 9 API3:2023 Broken Object Property Level Authorization - Part 1
Lecture 10 API3:2023 Broken Object Property Level Authorization - Part 2 (Practice)
Lecture 11 API4:2023 Unrestricted Resource Consumption - Part 1
Lecture 12 API4:2023 Unrestricted Resource Consumption - Part 2 (Practice)
Lecture 13 API5:2023 Broken Function Level Authorization - Part 1
Lecture 14 API5:2023 Broken Function Level Authorization - Part 2 (Practice)
Lecture 15 API6:2023 Unrestricted Access to Sensitive Business Flows - Part 1
Lecture 16 API6:2023 Unrestricted Access to Sensitive Business Flows - Part 2
Lecture 17 API6:2023 Unrestricted Access to Sensitive Business Flows - Part 3 (Practice)
Lecture 18 API7:2023 - Server Side Request Forgery
Lecture 19 API8:2023 - Security Misconfiguration
Lecture 20 API9:2023 Improper Inventory Management - Part 1
Lecture 21 Improper Inventory Management - Part 2 (Practice)
Lecture 22 API10:2023 Unsafe Consumption of APIs - Part 1
Lecture 23 API10:2023 Unsafe Consumption of APIs - Part 2 (Practice)
Section 3: Extra Materials: OWASP Top 10 2021
Lecture 24 OWASP Top 10: Overview
Lecture 25 Broken Access Control
Lecture 26 Cryptography Failures (Theory, Sensitive Data, Data Breach, Types of Failures)
Lecture 27 Cryptography Failures (Practical Examples, SQL Injections, TLS/SSL, HTTPS)
Lecture 28 Cryptography Failures (Examples, Password Encryption, Hashing, Salting)
Lecture 29 Injection (Overview, Fuzzing, CWEs, Impact, Injection Types, Command Injection)
Lecture 30 Injection (Cross Site Scripting, Types of XSS, SQL, JPA, NoSQL Injections)
Lecture 31 Injection (XPath Injection, Log Injection, Input Validation)
Lecture 32 Insecure Design (Overivew, CWEs, Shift Left Security, Threat Modeling Manifesto)
Lecture 33 Insecure Design (Secure Design Process, Security Controls, Metrics, Examples)
Lecture 34 Security Misconfiguration (Overview, CWEs, Types, Real-life attacks)
Lecture 35 Security Misconfiguration (Hardening, Zero Trust, Defense in Depth, Practice)
Lecture 36 Vulnerable & Outdated Components
Lecture 37 Identification & Authentication Failures
Lecture 38 Software & Data Integrity Failures
Lecture 39 Security Logging & Monitoring Failures
Lecture 40 Server-Side Request Forgery (SSRF)
Section 4: Bonus section
Lecture 41 Bonus lesson
Developers looking to enhance their API security skills,Security professionals seeking to understand the latest API vulnerabilities,Software engineers interested in building secure applications,Students and beginners eager to learn about API security best practices,Tech leads and architects wanting to implement robust security measures in their projects

https://ddownload.com/9kfd1flcq7uy/Udemy_OWASP_API_Security_Top_10_2023_Comprehensive_Security_Guide_2024-9_Downloadly.ir.part1.rar
https://ddownload.com/n6lg17qdwee1/Udemy_OWASP_API_Security_Top_10_2023_Comprehensive_Security_Guide_2024-9_Downloadly.ir.part2.rar
https://ddownload.com/v63qdid8gm2l/Udemy_OWASP_API_Security_Top_10_2023_Comprehensive_Security_Guide_2024-9_Downloadly.ir.part3.rar
https://ddownload.com/fb32p6mmbp7m/Udemy_OWASP_API_Security_Top_10_2023_Comprehensive_Security_Guide_2024-9_Downloadly.ir.part4.rar
https://rapidgator.net/file/7b11c66c8ea7c4de0c72d1c32c64f03b/Udemy_OWASP_API_Security_Top_10_2023_Comprehensive_Security_Guide_2024-9_Downloadly.ir.part1.rar
https://rapidgator.net/file/447ac870cca39b54be3141a588d8bb02/Udemy_OWASP_API_Security_Top_10_2023_Comprehensive_Security_Guide_2024-9_Downloadly.ir.part2.rar
https://rapidgator.net/file/91c38fe2e817a33ddffb1f83efb616ab/Udemy_OWASP_API_Security_Top_10_2023_Comprehensive_Security_Guide_2024-9_Downloadly.ir.part3.rar
https://rapidgator.net/file/64859c9d6063240bd3003011588fad65/Udemy_OWASP_API_Security_Top_10_2023_Comprehensive_Security_Guide_2024-9_Downloadly.ir.part4.rar
https://turbobit.net/k0bcxas1k1en/Udemy_OWASP_API_Security_Top_10_2023_Comprehensive_Security_Guide_2024-9_Downloadly.ir.part1.rar.html
https://turbobit.net/xypghk5tf504/Udemy_OWASP_API_Security_Top_10_2023_Comprehensive_Security_Guide_2024-9_Downloadly.ir.part2.rar.html
https://turbobit.net/jl2j0lg9j60x/Udemy_OWASP_API_Security_Top_10_2023_Comprehensive_Security_Guide_2024-9_Downloadly.ir.part3.rar.html
https://turbobit.net/d7e4ypt02sdf/Udemy_OWASP_API_Security_Top_10_2023_Comprehensive_Security_Guide_2024-9_Downloadly.ir.part4.rar.html
